Terraform is an open-source Infrastructure as Code (IaC) tool from HashiCorp that allows you to define and provision infrastructure using configuration files, enabling automation and management of resources across various cloud providers and on-premises environments.Just for you to be updated,FYI, IBM acquired HashiCorp, the creator of Terraform, in a deal valued at $6.4 billion, which was finalized on February 27, 2025. IBM plans to leverage HashiCorp’s capabilities, including Terraform and Vault, to enhance its hybrid cloud and AI offerings. If you’ve ever felt overwhelmed managing your cloud resources, you’re not alone. The emergence of Infrastructure as Code (IaC) has truly revolutionized the way we deploy and maintain infrastructure, and Terraform sits right at the heart of this transformation.
However, keeping your Terraform code neat, efficient, and secure in larger environments can sometimes feel like a juggling act. Thankfully, there’s a suite of tools available to help you maintain best practices throughout your workflow. In this article, we’ll explore some of these tools—each designed to make your Terraform journey smoother, more collaborative, and far less risky.
1. Identify Potential Cloud-Specific Errors and Linting with TFLint

TFLint is an advanced static analysis tool created specifically for Terraform. While terraform validate focuses on basic checks like syntax and resource structure, TFLint digs deeper to catch subtle problems you might otherwise miss.
Key Benefits
- Provider-Specific Rules: Includes built-in checks for major cloud providers (AWS, Azure, GCP) and flags region-specific resource issues.
- Custom Rule Support: Craft custom policies to enforce your internal standards and best practices.
- CI/CD Integration: Seamlessly integrate with continuous integration pipelines to block problematic code from moving forward.
Getting Started with TFLint
Installation is straightforward. For macOS, you can use:
brew install tflint
For Windows:
choco install tflint
Or via a simple script for Linux OS:
curl -s https://raw.githubusercontent.com/terraform-linters/tflint/master/install_linux.sh | bash

Create a .tflint.hcl in your project root to configure rules:
plugin "terraform" {
enabled = true
preset = "recommended"
}
plugin "aws" {
enabled = true
version = "0.38.0"
source = "github.com/terraform-linters/tflint-ruleset-aws"
}
plugin "azurerm" {
enabled = true
version = "0.27.0"
source = "github.com/terraform-linters/tflint-ruleset-azurerm"
}
plugin "google" {
enabled = true
version = "0.31.0"
source = "github.com/terraform-linters/tflint-ruleset-google"
}
Before you run the command below, ensure you have installed the required plugin, else , you might get error like this in quotes ” Failed to run in .; exit status 1
Failed to initialize plugins; Plugin “aws” not found. Did you run “tflint –init”? , Run tflint –init as seen in the image below
 “Then run TFLint regularly to see the output in the image below:
“Then run TFLint regularly to see the output in the image below:
tflint --recursive

2. Automated Documentation with terraform-docs

terraform-docs automatically generates documentation from your Terraform modules, making it much easier for teams to understand how to use and configure your code. This prevents the dreaded “documentation drift” where README files go out of date.
Key Benefits
- Consistent Documentation: Creates standard-format docs for every module in your codebase.
- Always Current: Pulls from your code to ensure the docs align with actual configurations.
- Multiple Formats: Exports to Markdown, JSON, YAML, and more, fitting into different workflows.
Getting Started with terraform-docs
For macOS:
brew install terraform-docs
For Linux via Snap:
sudo snap install terraform-docs
Using Go:
go install github.com/terraform-docs/terraform-docs@latest
Windows
If you are a Windows user:
Scoop
scoop bucket add terraform-docs https://github.com/terraform-docs/scoop-bucket
scoop install terraform-docs
Chocolatey
choco install terraform-docs
Bash
terraform-docs completion bash > ~/.terraform-docs-completion
source ~/.terraform-docs-completion
# or the one-liner below
source <(terraform-docs completion bash)
Docker
docker run --rm --volume "$(pwd):/terraform-docs" -u $(id -u) quay.io/terraform-docs/terraform-docs:0.19.0 markdown /terraform-docs
If output.file is not enabled for this module, you can redirect the generated output to a file:
docker run --rm --volume "$(pwd):/terraform-docs" -u $(id -u) quay.io/terraform-docs/terraform-docs:0.19.0 markdown /terraform-docs > doc.md
Add a .terraform-docs.yml for configuration:
formatter: "markdown table"
output:
file: "README.md"
mode: inject
settings:
indent: 3
Generate documentation with the command below to obtain the output seen :
terraform-docs markdown . > README.md

You can also set up pre-commit hooks so your docs are refreshed before every commit.
3. Security Scanning
3.1 Terrascan
Terrascan is an open-source security scanner for Infrastructure as Code that detects policy violations and security misconfigurations.

Key Features
- Extensive Policy Library: Bundles hundreds of checks aligned with industry standards.
- Multiplatform: Supports Terraform, Kubernetes, CloudFormation, and more.
- Custom Policies: Leverage Rego (OPA) to create organization-specific security rules.
Getting started is simple:
brew install terrascan
Or use Docker:
docker pull accurics/terrascan
Or use Curl:
curl -L "$(curl -s https://api.github.com/repos/tenable/terrascan/releases/latest | grep -o -E "https://.+?_Darwin_x86_64.tar.gz")" > terrascan.tar.gz
tar -xf terrascan.tar.gz terrascan && rm terrascan.tar.gz
sudo install terrascan /usr/local/bin && rm terrascan
terrascan

Then scan your Terraform files to see outupt similar to the image below:
terrascan scan -d /path/to/terraform/files

3.2 Trivy
Trivy is a versatile security tool that scans not only Terraform configurations but also container images and file systems for vulnerabilities.
Key Features
- Broad Coverage: Catches threats across multiple resource types.
- Misconfiguration Detection: Flags any security gaps in your Terraform code.
- Fast and Straightforward: Minimal setup with quick scan times.
Installation:
brew install trivy
Using Apt:
apt-get install trivy
Or Via Install Script (Official):
curl -sfL https://raw.githubusercontent.com/aquasecurity/trivy/main/contrib/install.sh | sudo sh -s -- -b /usr/local/bin v0.61.0
Running the curl command will give you output similar to:
aquasecurity/trivy info checking GitHub for tag 'v0.61.0'
aquasecurity/trivy info found version: 0.61.0 for v0.61.0/Linux/64bit
aquasecurity/trivy info installed /usr/local/bin/trivy
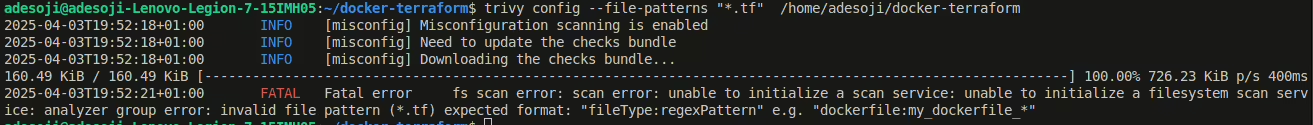
Then Run the command below to scan:
trivy config --file-patterns "*.tf" /path/to/terraform/files
4. tfenv — Terraform Version Manager
tfenv helps you effortlessly juggle multiple Terraform versions. This is vital for maintaining consistent behavior, especially when working across various projects and teams.
Key Features
- Easy Version Switching: Install, remove, and switch between versions in a snap.
- Project-Specific Versions: Automatically selects the correct version using a
.terraform-versionfile. - Simple Setup: Works on macOS, Linux, and Windows (via WSL).
Example setup:
git clone https://github.com/tfutils/tfenv.git ~/.tfenv
echo 'export PATH="$HOME/.tfenv/bin:$PATH"' >> ~/.bash_profile
Or via Homebrew:
brew install tfenv
Install a specific Terraform version and switch to it:
tfenv install 1.5.7
tfenv use 1.5.7
Put a version in a .terraform-version file to ensure everyone uses the same one:
echo "1.5.7" > .terraform-version
tfenv install
5. Checkov

Checkov is a static code analyzer that catches misconfigurations in your infrastructure before they reach production.
Key Features
- Huge Policy Library: Comes with more than 1,000 policies to ensure compliance.
- Custom Rules: Easily write your own policies in Python.
- Skip Mechanism: Temporarily bypass specific checks with clear justifications.
Install Checkov:
pip install checkov
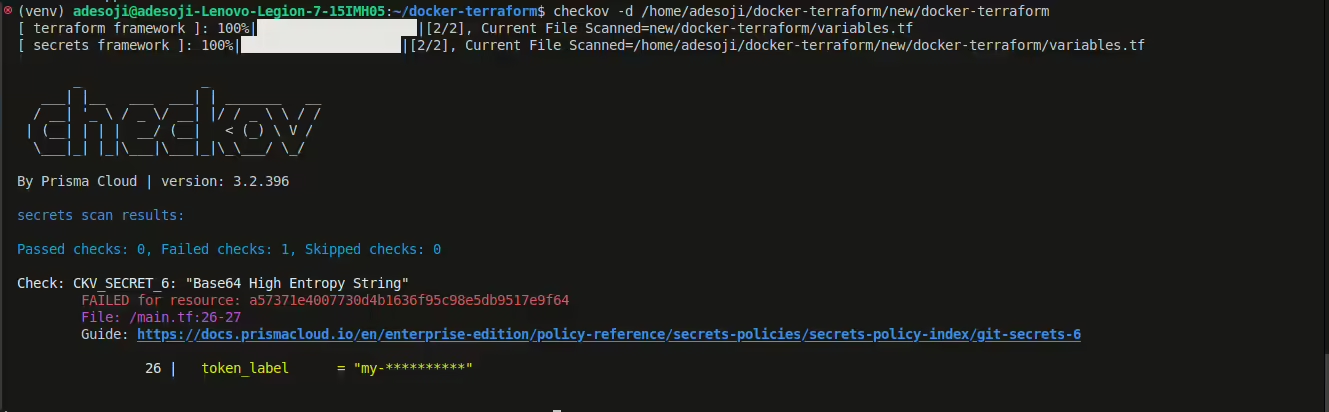
Then run:
checkov -d /path/to/terraform/files
6. Pre-commit Hooks
pre-commit is a framework that automates code checks (like formatting, linting, or generating docs) before each commit. This ensures you don’t accidentally commit broken or poorly formatted code.
Example .pre-commit-config.yaml:
repos:
- repo: https://github.com/pre-commit/pre-commit-hooks
rev: v4.4.0
hooks:
- id: trailing-whitespace
- id: end-of-file-fixer
- id: check-yaml
- repo: https://github.com/antonbabenko/pre-commit-terraform
rev: v1.77.1
hooks:
- id: terraform_fmt
- id: terraform_docs
- id: terraform_tflint
- id: terraform_validate
- id: terraform_checkov
7. Terragrunt

Terragrunt is a lightweight wrapper around Terraform that promotes the DRY principle (Don’t Repeat Yourself). It’s especially useful when orchestrating multiple modules or environments in a single repository. For various release of terragunt for your OS, click here here to download
Key Features
- Configuration Reuse: Encourages shared variables and minimized repetition.
- Remote State Management: Simplifies the process of managing backends.
- Dependency Management: Automatically handles dependencies across your Terraform modules.
Quick start:
brew install terragrunt
Example structure:
/root
terragrunt.hcl
/dev
terragrunt.hcl
/staging
terragrunt.hcl
/prod
terragrunt.hcl
8. Infracost
Infracost estimates cloud costs for your Terraform resources. It’s an eye-opener when you realize how critical budgeting can be in large-scale operations.

Key Features
- Detailed Cost Breakdown: Understand the cost of individual resources.
- CI/CD Integration: Generate cost change reports right in your pull requests.
- Multi-Cloud Support: Works with AWS, Azure, GCP, and more.
Installation:
The easiest way is to use our install script:
# Downloads the CLI based on your OS/arch and puts it in /usr/local/bin curl -fsSL https://raw.githubusercontent.com/infracost/infracost/master/scripts/install.sh | sh
Or you can install it manually:
- Download the archive for your platform from our releases.
- Unarchive and copy it to one of the directories in your
$PATH, e.g./usr/local/bin:
tar xzf infracost-linux-amd64.tar.gz -C /tmp mv /tmp/infracost-linux-amd64 /usr/local/bin/infracost
Windows (Chocolatey):
choco install infracost
Authenticate:
Register for a free API key, which is used by the CLI to retrieve prices from our Cloud Pricing API, e.g., to get prices for instance types.
- No cloud credentials or secrets are sent to the API.
- Infracost does not make any changes to your Terraform state or cloud resources.
infracost auth login
Docker:
docker pull infracost/infracost:ci-latest
docker run --rm \ -e INFRACOST_API_KEY=see_following_step_on_how_to_get_this \ -v $PWD/:/code/ infracost/infracost:ci-latest breakdown --path /code/
Generate cost estimates:
infracost breakdown --path /path/to/terraform
9. Terraform Compliance

Terraform Compliance is a specialized tool that checks Terraform configurations against compliance rules using a behavior-driven approach (BDD).
Key Features
- BDD-Style Tests: Write rules in readable language.
- Security Focus: Strictly enforces security guidelines.
- Seamless CI/CD Integration: Include it in your pipeline to keep your infrastructure in check.
Here’s an example below:
Feature: AWS S3 Bucket Security
Scenario: Ensure S3 buckets have encryption enabled
Given I have AWS S3 Bucket defined
Then it must have encryption enabled
Integrating Everything Into Your Workflow
To maximize their benefits, incorporate these tools both locally and in your CI/CD pipelines:
- Local Development: Use pre-commit hooks for immediate feedback on formatting, linting, and docs.
- CI/CD Pipeline: Automate all checks (linting, scanning, docs generation, cost estimation) to stop errors early.
- Code Reviews: Attach findings and reports to your pull requests for informed reviews.
- Frequent Audits: Run weekly or monthly full-code scans to maintain a healthy infrastructure.
A sample CI/CD stage:
terraform-quality:
stage: validate
script:
- terraform init -backend=false
- terraform validate
- tflint
- checkov -d .
- terrascan scan -d .
- terraform-docs markdown . > README.md
- infracost breakdown --path .
artifacts:
paths:
- README.md
- infracost-report.html
Conclusion
It’s easy to feel overwhelmed by the sheer volume of tasks and considerations when managing production-grade Terraform. But using the right tools—like TFLint for linting, terraform-docs for documentation, Terrascan and Trivy for security checks, tfenv for version control, and so on—can turn that chaos into clarity.
Each tool mentioned here plays a unique role in delivering a clean, safe, and future-proof infrastructure. Once integrated into your everyday processes, you’ll find that these tools not only prevent mishaps but also inspire greater collaboration and confidence across your team.
What has made your Terraform journey smoother? Feel free to share your experiences and recommendations in the comments. Let’s learn from each other to build more robust, secure, and cost-effective infrastructures.
